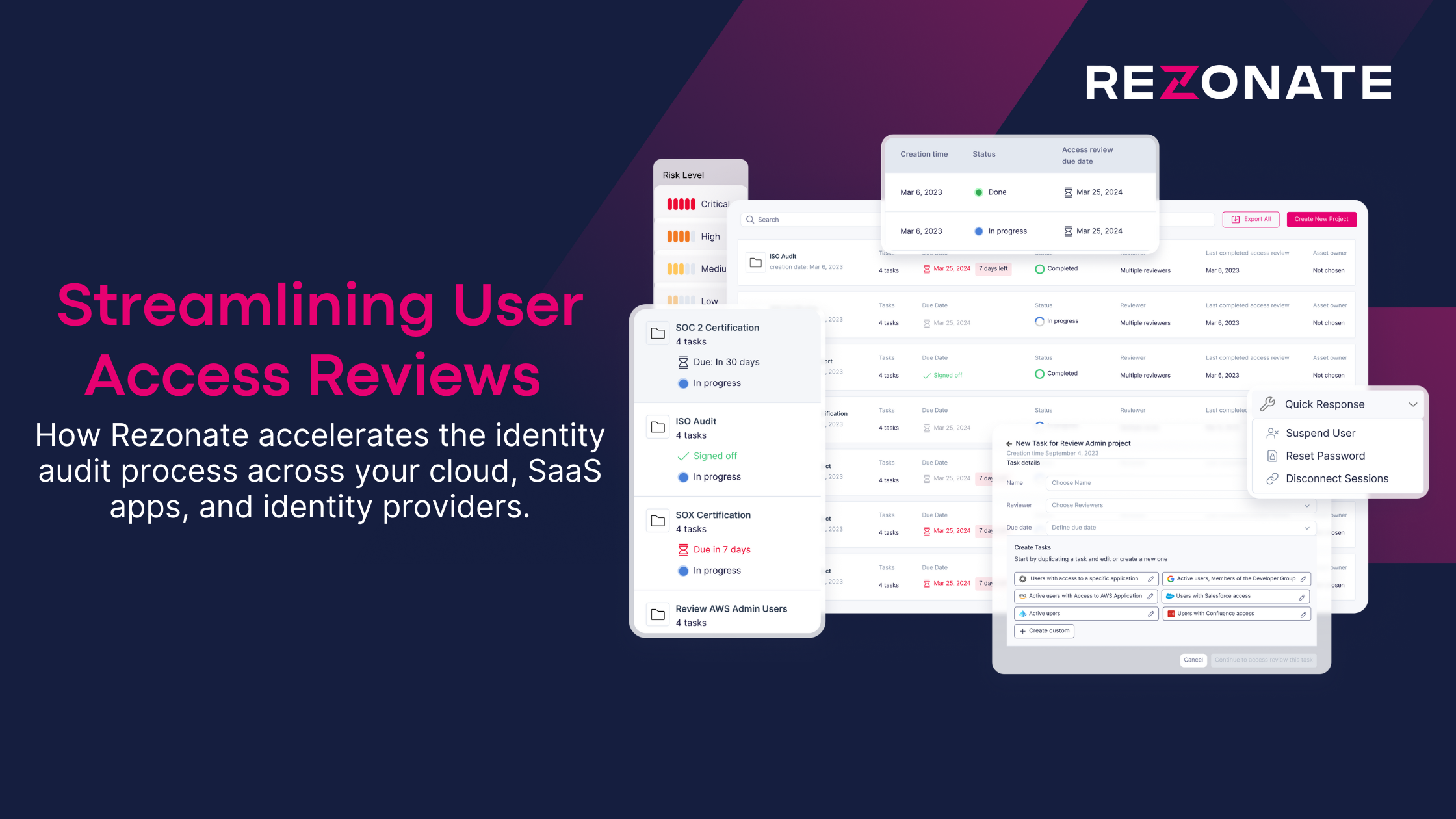
Blog
November 13, 2024
Today marks a monumental day in our journey that will redefine the future of identity security, taking our company, customers, and partners to new heights. We are excited to share that Silverfort has acquired Rezonate!