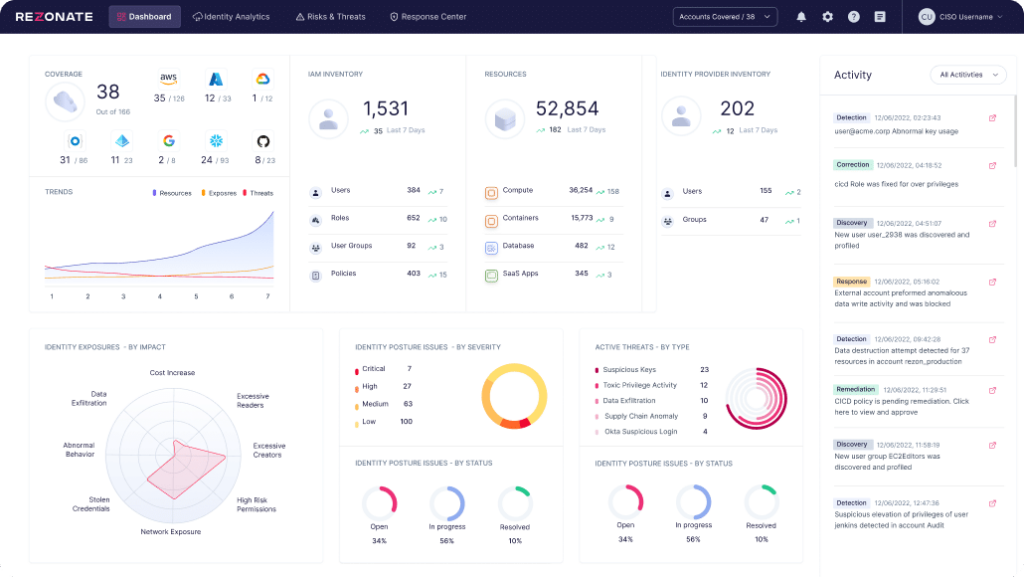
OVERVIEW
Monitor Identity Privileges and Activities
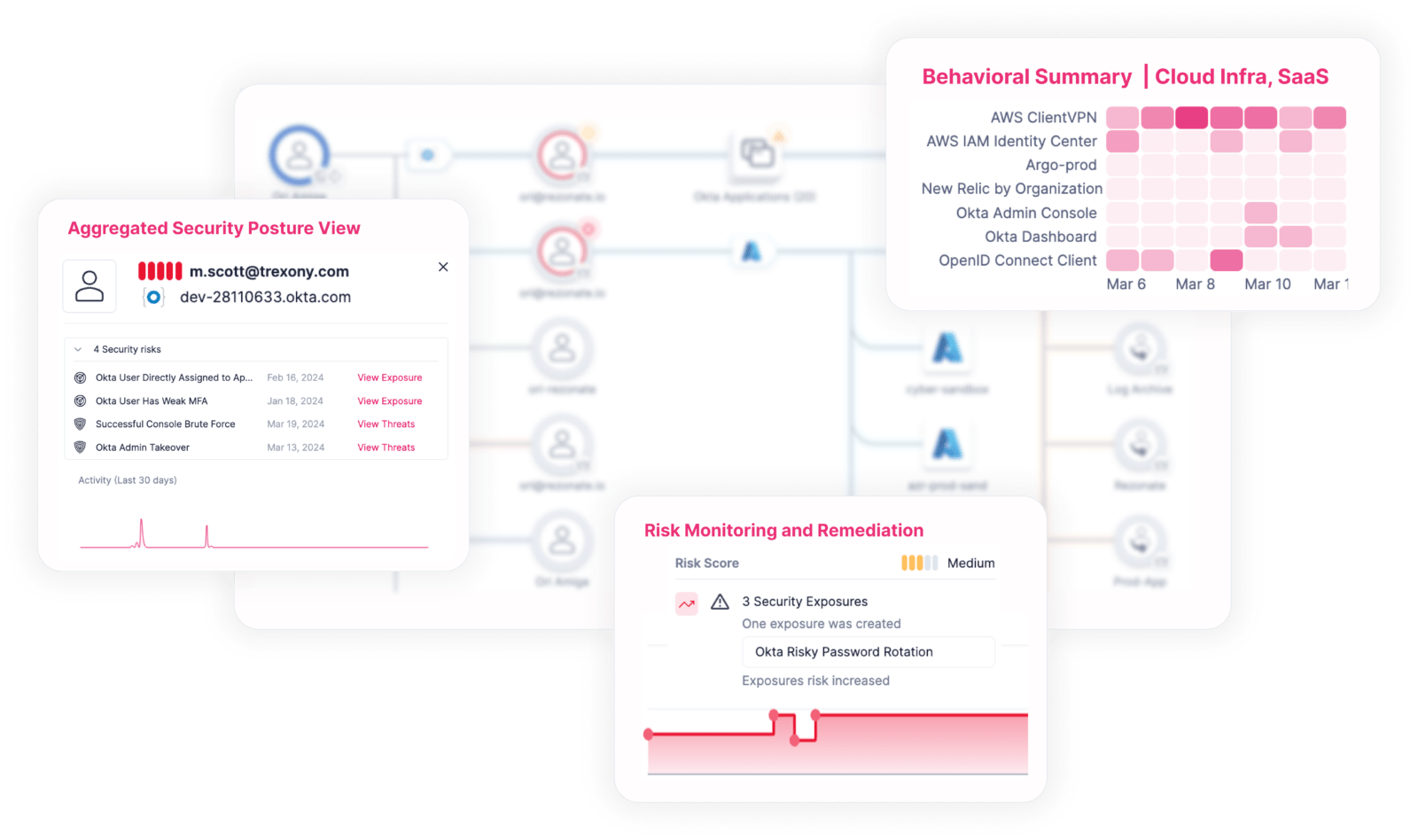
Eliminate Blind Spots
Take control of your identity security with a unified view into access insights across your cloud platforms, SaaS, and identity providers. This makes it easy with one platform that correlates all of the identity and access data across so you can explore access pathways, identity activities, privileges, and security exposures.
Unified Identity Visibility
Unified Visibility Features
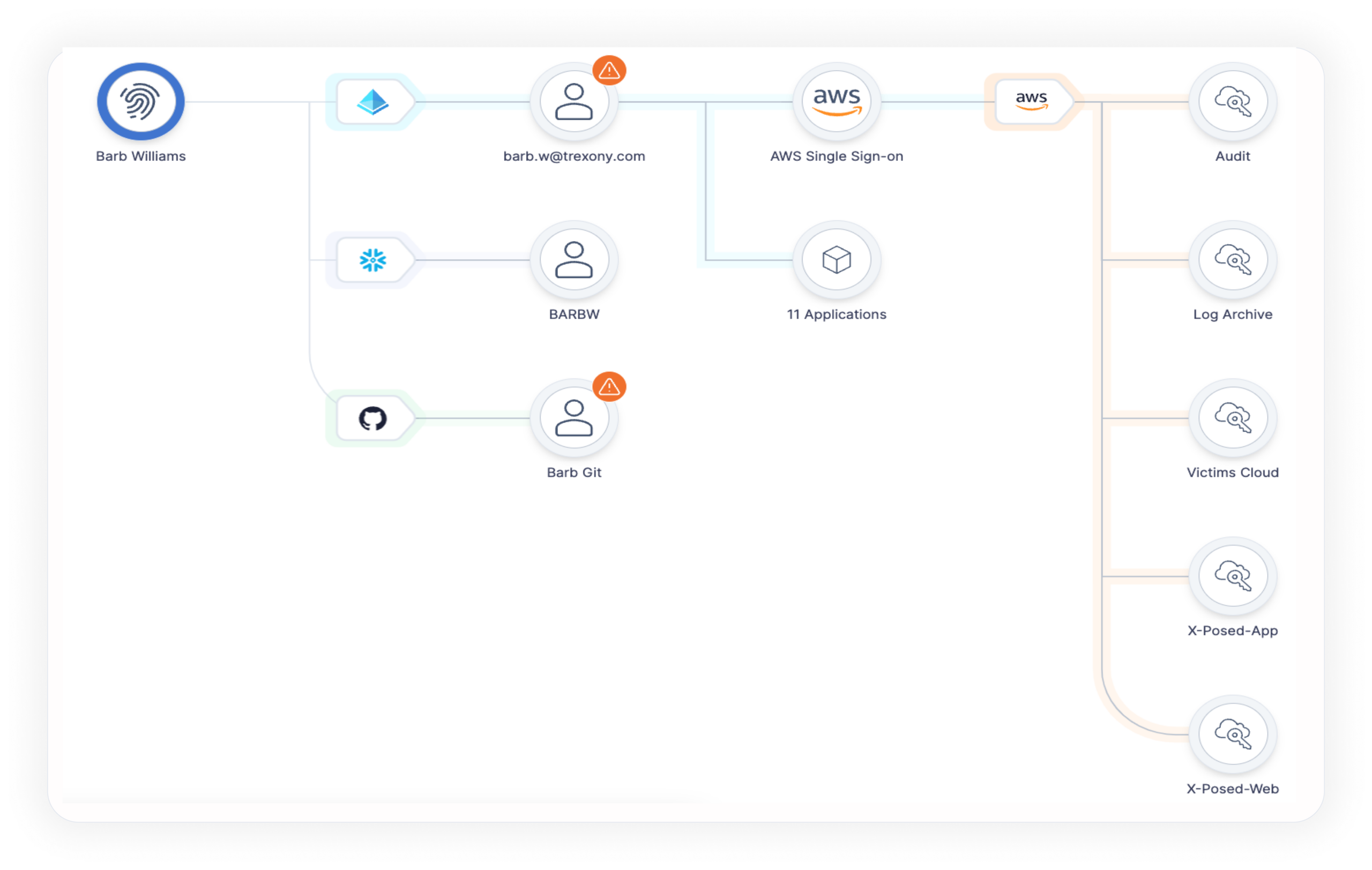
Identity Storyline
Access review and effective privileges summary
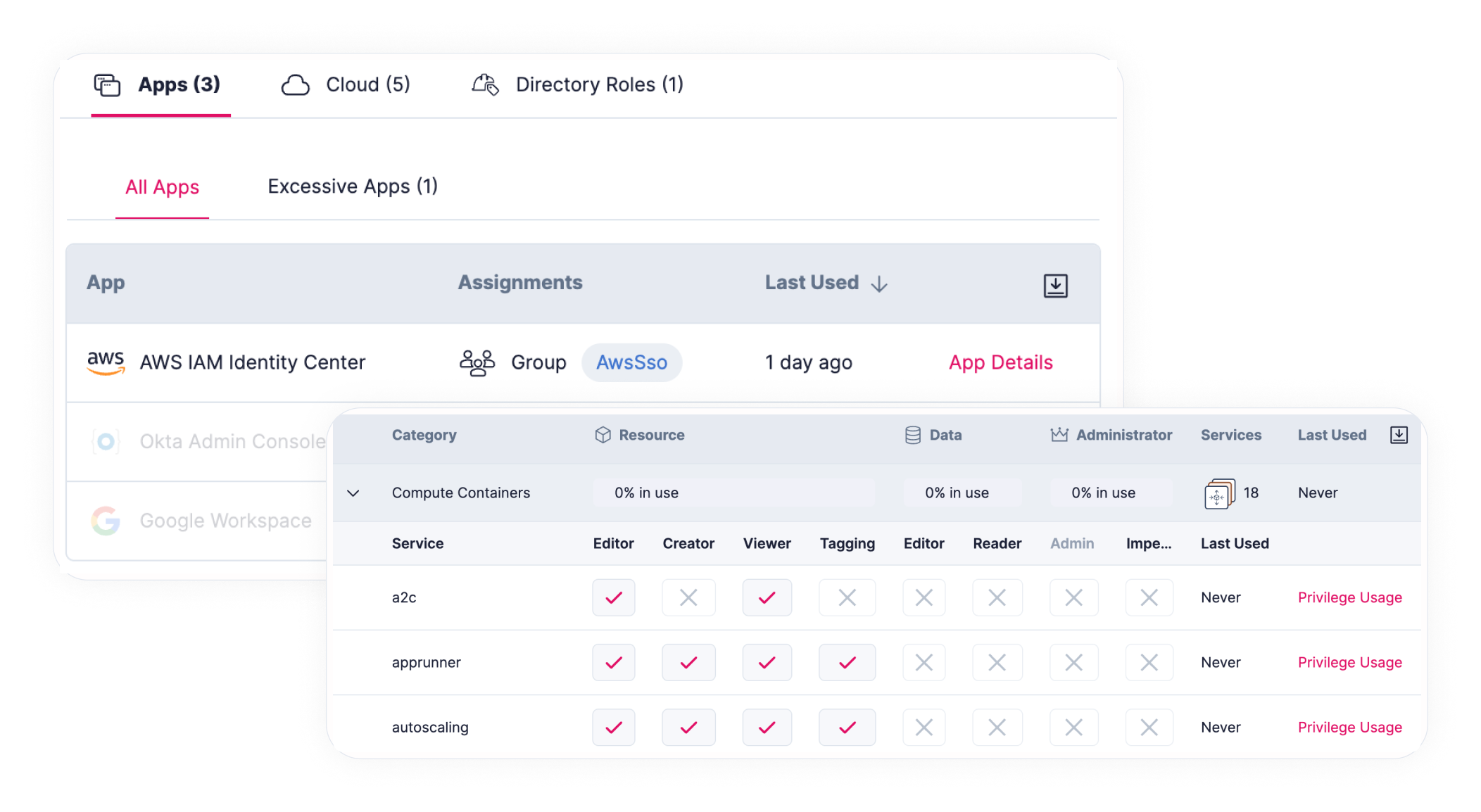
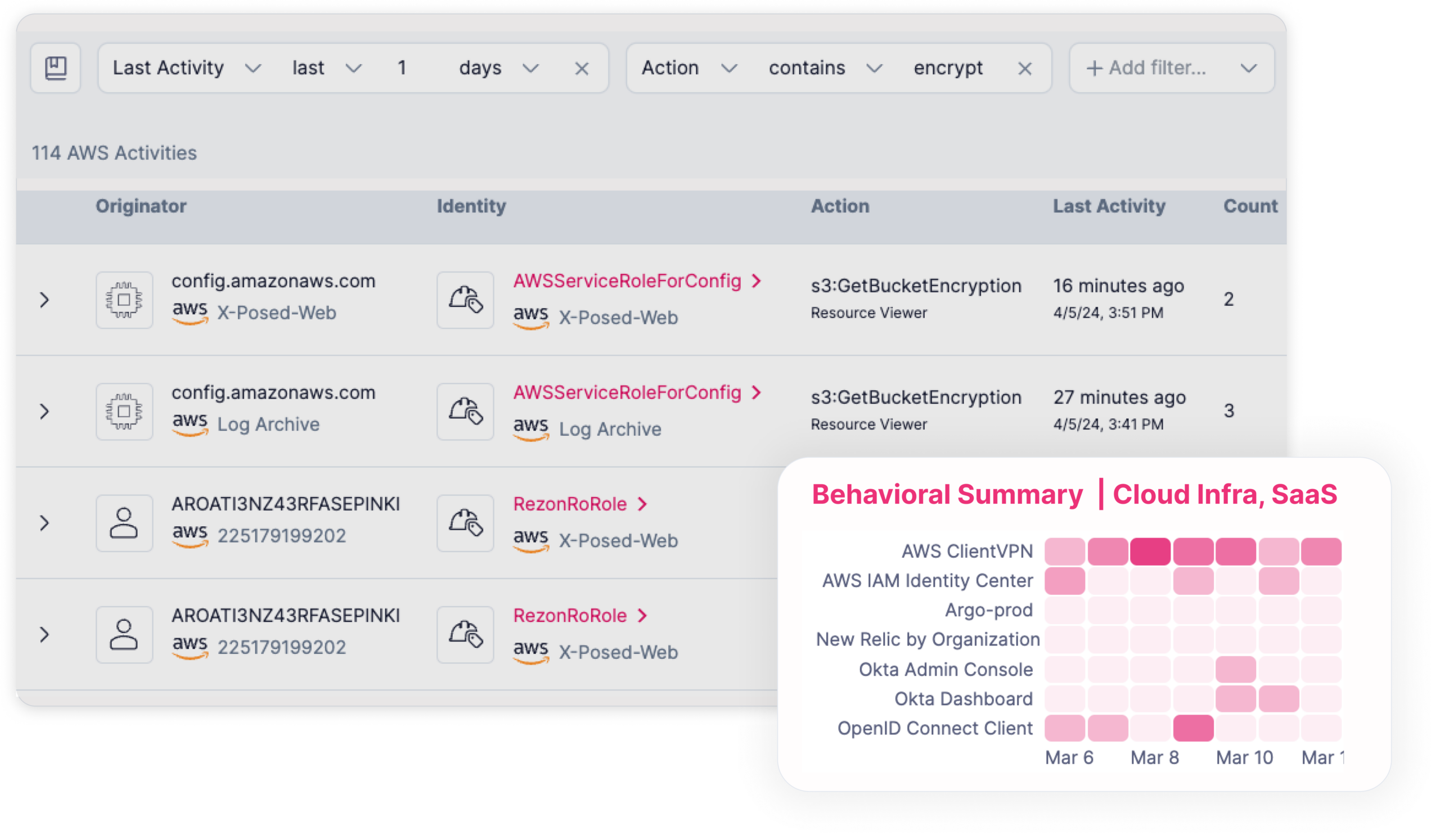
Activities and log analysis
Continuous monitoring
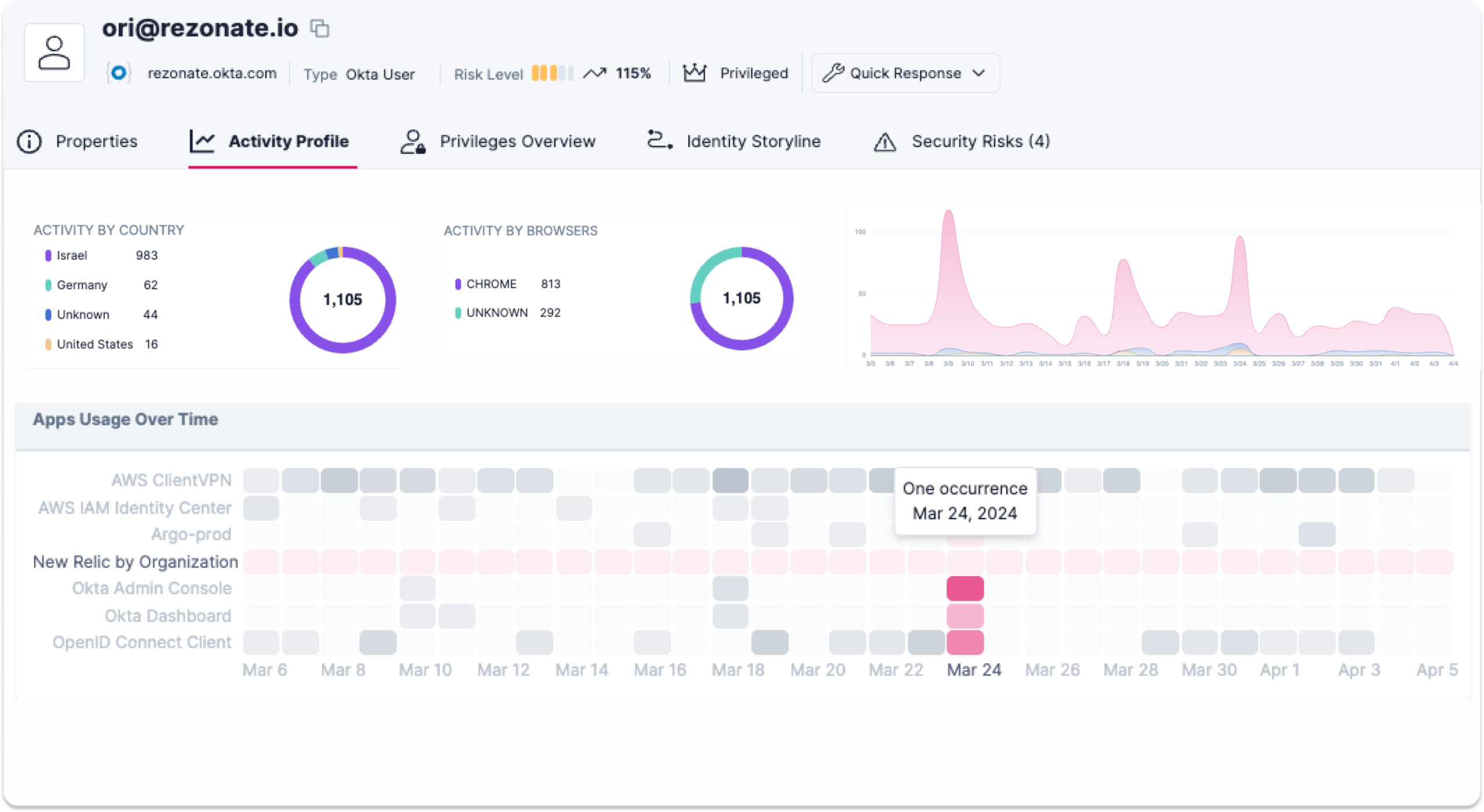
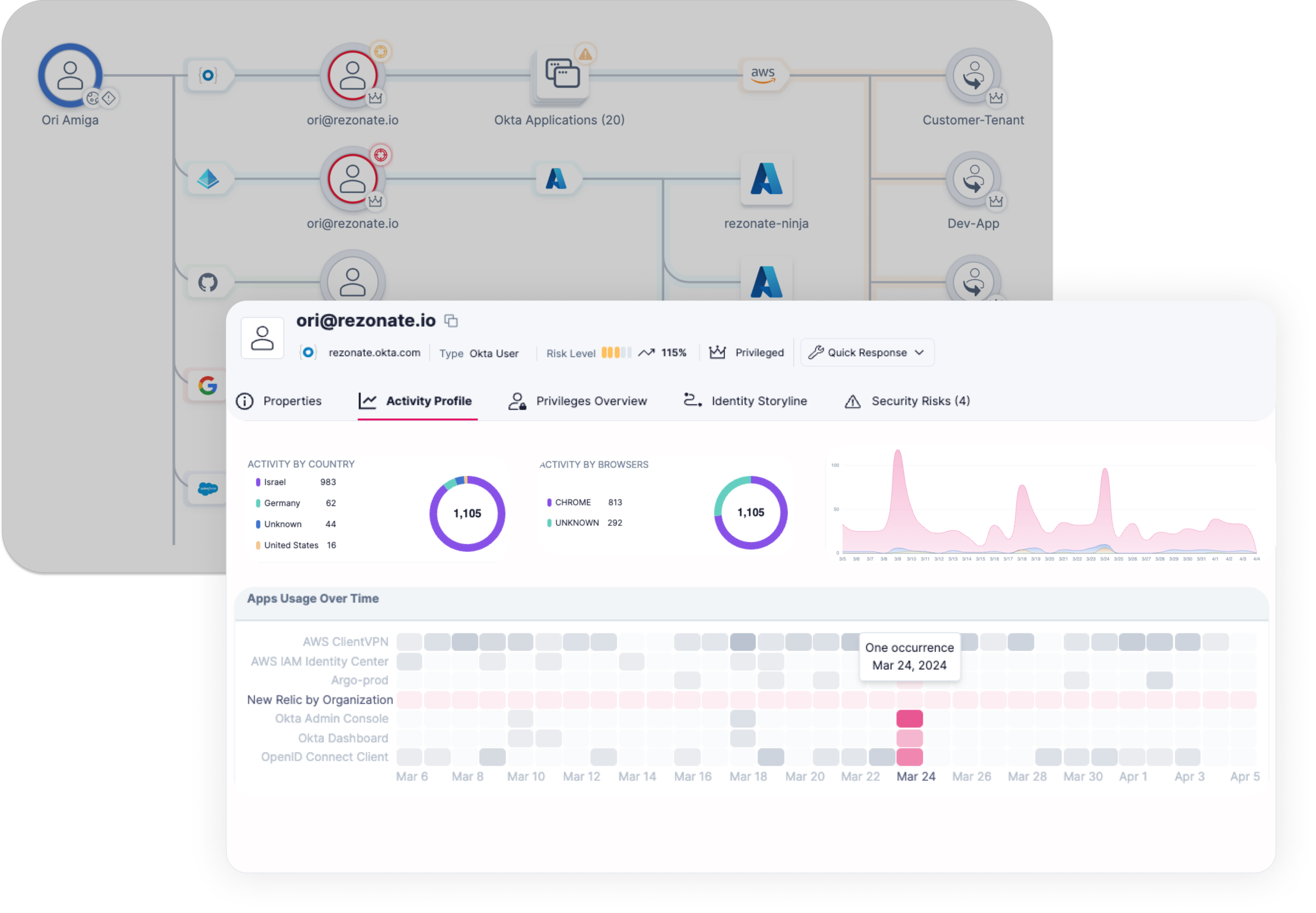
Granular visibility
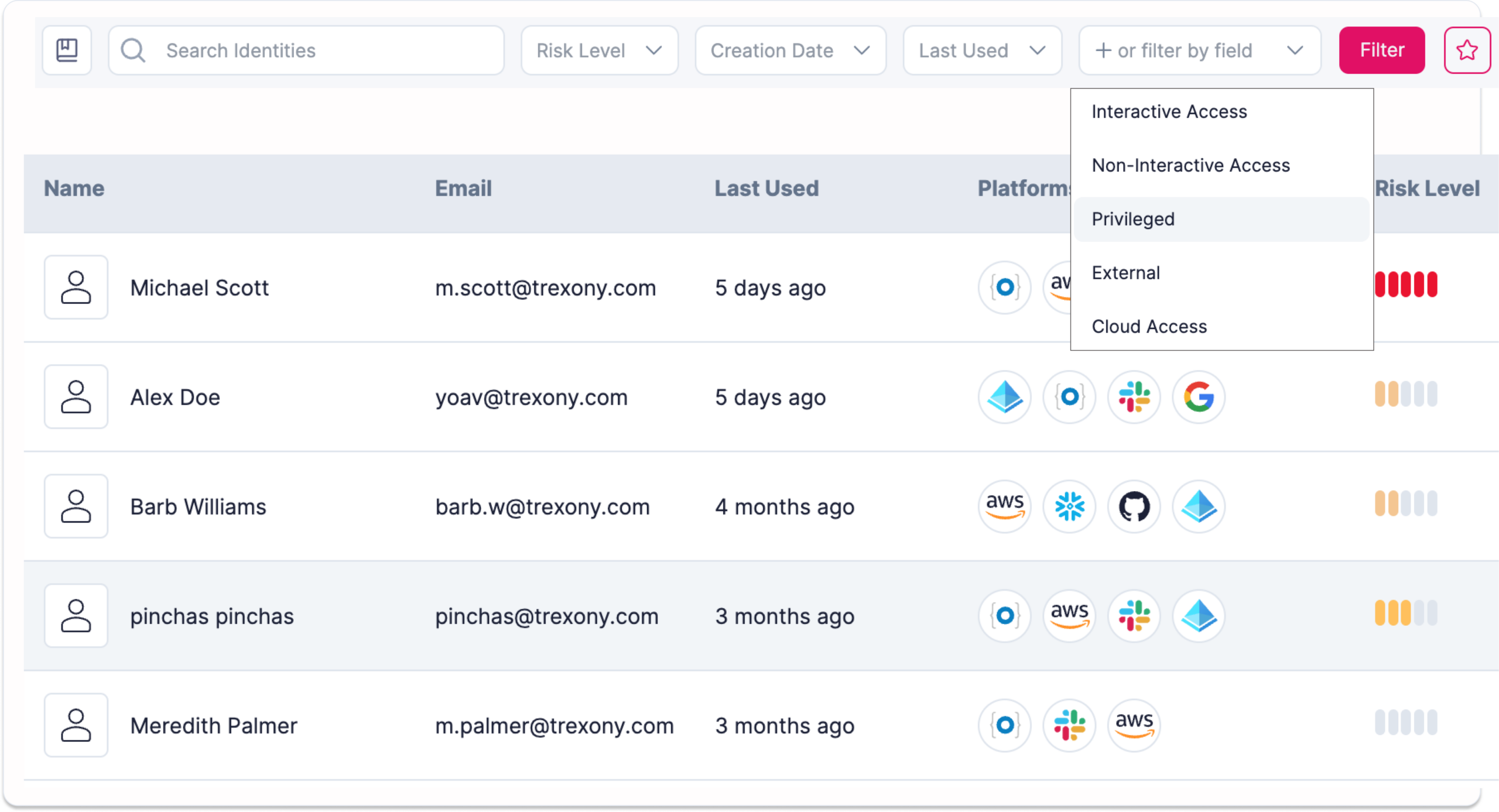
Interactive reporting
Trusted by Leaders

Paul Groisman
Sr. Director Cyber Security, Fubo
"Rezonate combines identity threat detection and posture management to reduce exposure time and optimize our response to suspicious activities. The robust remediation workflows and the UI, make the platform an important asset in our line of defense."

Dor Kitenberg
Head of Cyber Security, Beamtree
"Secure access to sensitive information and visibility into identities in health data analytics cannot be overstated. The frequent acquisitions and integrations of various companies and their identity stacks add to our complexity and governance efforts. Rezonate solves our extended identity attack surface, enhancing our security process without slowing us down, keeping us vigilant against threats."

Sam Curry
CISO, zScaler
"Rezonate brings a new approach to cloud identity protection. The innovation and simplicity it delivers enable organizations of all sizes and all maturity levels to reduce cloud identity and access risk. By embracing the dynamic cloud and applying that same agility towards its security, Rezonate is really changing the way cloud security is thought of today. The time to protect cloud identities and access is now."

Olivier Martinet,
CISO, TX Group
"With Rezonate we can finally see and understand an end-to-end view of our cloud identities and their respective risk - across our identity provider all the way to our multi-account AWS infrastructure - in real time. Our DevOps and security teams are enabled to work hand-in-hand to eliminate blindspots and accelerate remediations."

Alexander Sorochan
Head of DevSecOps, PayMe
"Within hours of deployment, we understood the complete picture of our cross-cloud identity and access risks. Our DevOps team uses Rezonate daily to understand context and prioritize critical risks. We are now 10X faster and more effective in remediating security gaps."
GET A PERSONALIZED DEMO
Ready to see Rezonate in action?
“Rezonate combines identity threat detection and posture management to reduce exposure time and optimize our response to suspicious activities. The robust remediation workflows and the UI, make the platform an important asset in our line of defense.”
Paul Groisman
Sr. Director Cyber Security, Fubo