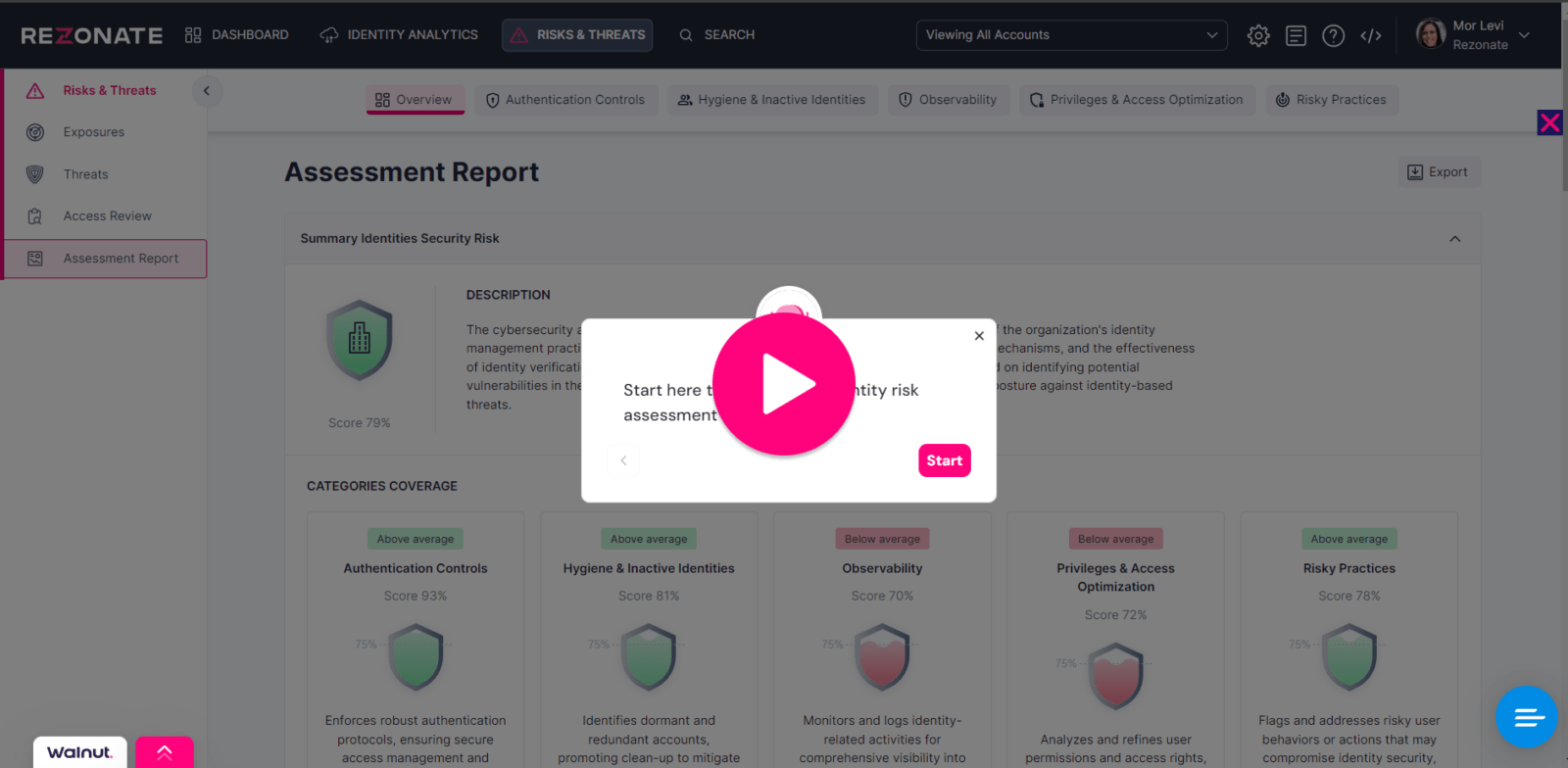
Interactive Identity Security Assessment
Our interactive identity security assessment will give you a baseline understanding of your current identity security posture in five key areas. It enables you to prioritize and eliminate the most critical opportunities for attackers to compromise your identities across your cloud infrastructure, SaaS applications, and identity provider platforms.
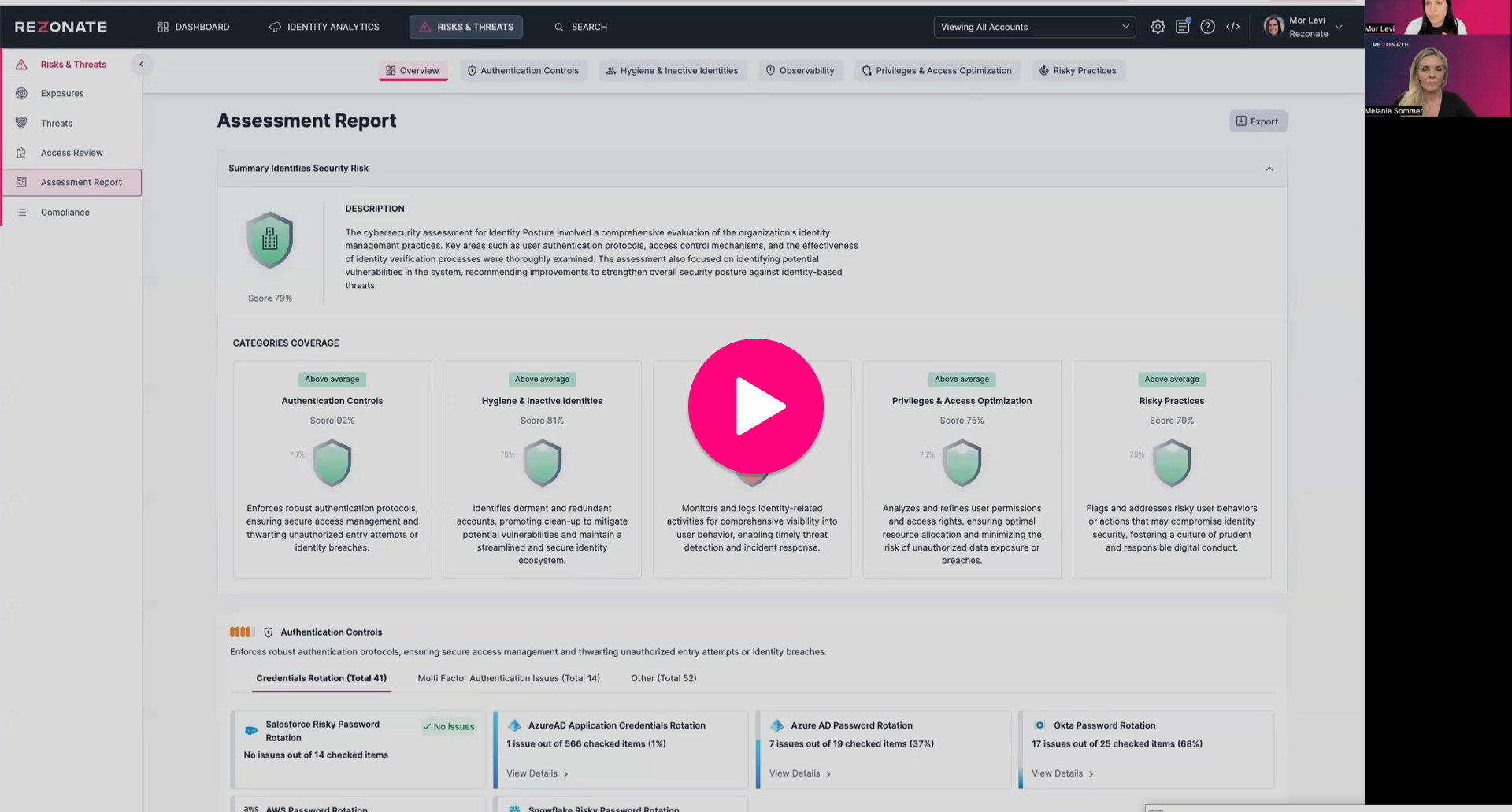
Find and Eliminate Your Identity Weak Spots
Whether you’re a new CISO wanting a quick snapshot of your identity security posture, in the midst of an acquisition, preparing for an audit, planning your next security program or you are recovering from a breach, this interactive experience can be an invaluable tool to help you strengthen your identity attack surface and prevent future attacks.
How It Works
Surface your riskiest areas with a spotlight on your top identities at risk of compromise.
Review your privileged identities at risk. Easily discover shadow admins and over-privileged users and enforce least privilege policy.
Review both human and machine identities and their access privileges and activity to detect risky external access to your cloud infrastructure and SaaS applications.
Remediate stale accounts and expired or weak security controls. Spot accounts lacking MFA and other security and compliance access requirements that aren’t up to policy.
80% of Breaches Start with Compromised Identities
Where are you currently at risk? Don’t wait until it’s too late!
Request your FREE Identity Security Assessment
Get started today! We’ll show you where your top identity risks are across AWS, Azure Cloud, Entra ID, Google Workspace, and Okta.
Trusted by Leaders

Paul Groisman
Sr. Director Cyber Security, Fubo
"Rezonate combines identity threat detection and posture management to reduce exposure time and optimize our response to suspicious activities. The robust remediation workflows and the UI, make the platform an important asset in our line of defense."

Dor Kitenberg
Head of Cyber Security, Beamtree
"Secure access to sensitive information and visibility into identities in health data analytics cannot be overstated. The frequent acquisitions and integrations of various companies and their identity stacks add to our complexity and governance efforts. Rezonate solves our extended identity attack surface, enhancing our security process without slowing us down, keeping us vigilant against threats."

Sam Curry
CISO, zScaler
"Rezonate brings a new approach to cloud identity protection. The innovation and simplicity it delivers enable organizations of all sizes and all maturity levels to reduce cloud identity and access risk. By embracing the dynamic cloud and applying that same agility towards its security, Rezonate is really changing the way cloud security is thought of today. The time to protect cloud identities and access is now."

Olivier Martinet,
CISO, TX Group
"With Rezonate we can finally see and understand an end-to-end view of our cloud identities and their respective risk - across our identity provider all the way to our multi-account AWS infrastructure - in real time. Our DevOps and security teams are enabled to work hand-in-hand to eliminate blindspots and accelerate remediations."

Alexander Sorochan
Head of DevSecOps, PayMe
"Within hours of deployment, we understood the complete picture of our cross-cloud identity and access risks. Our DevOps team uses Rezonate daily to understand context and prioritize critical risks. We are now 10X faster and more effective in remediating security gaps."