23 Oct

Top Identity Threat Exposures You Need to Address Now
Cloud environment intrusions have increased by 75% year on year, and it takes around 120 days for organizations to detect cyberattacks in the cloud. Additionally, the rise of remote working has only intensified the complexity. With employees connecting from various
15 Oct

100 Breakthrough Prompts for Your Best User Access Review
User access reviews are vital for maintaining robust identity security and ensuring compliance across your cloud and SaaS environments. With the growing complexity of managing identities—both human and machine—security teams must continuously monitor and validate access to minimize risks like
01 Oct
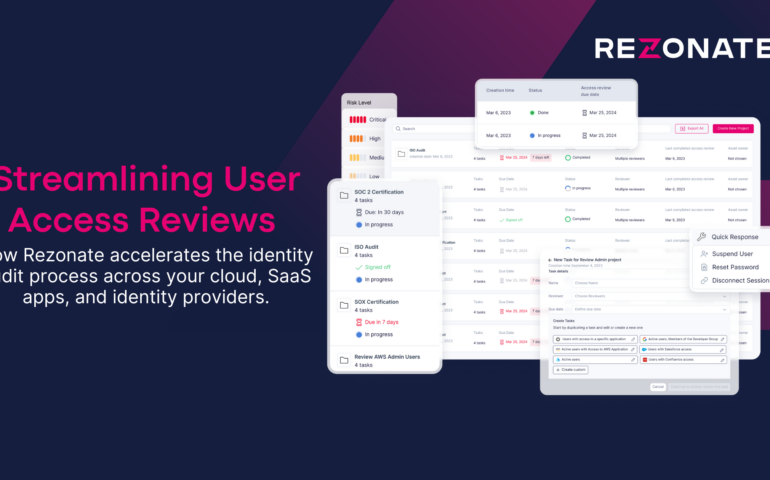
How to Unburden Your SaaS and Cloud Access Reviews
Managing access to cloud and SaaS applications is essential for securing critical business operations. Access reviews are a vital component of this process. They ensure employees have the appropriate permissions to do their jobs without exposing your organization to unnecessary
23 Sep

Google Workspace Security: Settings You Need to Ace Your Audit
Google Workspace security settings and controls are critical as it serves as an identity provider protecting important business tools like Gmail, Google Drive, Google Docs, and Google Meet. Designed for team collaboration, it offers features such as real-time document editing,
20 Apr

Eliminate Identity Blind Spots with Rezonate’s Interactive Identity Security Assessment
In today’s digital landscape, identity security is not just a necessity; it’s a critical battleground. With 80% of breaches stemming from compromised identities, it’s clear that traditional security measures are not enough. The number of identities to manage are increasing
27 Mar

Introducing Real-Time Identity-Centric Risk Profile – Designed To Help You Outpace Your Attackers
Identities face relentless threats, with attackers often outpacing defenders in speed. Their rapid tactics give them a breakout time of 84 minutes (according to CrowdStrike’s 2024 Global Threat Report1), making the fallout from an identity breach both significant and costly.

